What is TEN Protocol (TEN)?
What Is TEN Protocol?

(Source: tenprotocol)
TEN focuses on data access control—a function well-established in Web2 but often overlooked in Web3. It brings this capability to the decentralized world using hardware-based Trusted Execution Environments (TEE), programmable encryption, and a fully EVM-compatible execution framework. With these features, TEN aims to build the next generation of Layer 2 with Smart Transparency.
TEN Protocol Vision
Legacy blockchains emphasize making all data public. TEN argues that transparency does not mean all data should be open. By introducing Smart Transparency, TEN redesigns the smart contract framework.
The core idea is that smart contracts should control both computation rules and data access permissions. On TEN, contracts operate in an encrypted state, remain composable and automatable, and are fully compatible with Ethereum development practices. Developers can achieve Web2-level data control without sacrificing decentralization.
TEN Core Architecture
TEN uses three core technologies to define Layer 2.
1. Encrypted Execution — Fully Encrypted Contracts and Transaction States
On TEN, transactions, contract states, and application logic are encrypted during computation, preventing external inspection.
This means user activity is not tracked by on-chain analytics, and business strategies, game logic, and trading models stay confidential. Developers can build within the EVM-compatible framework without rewriting their applications. On TEN, MEV is not merely constrained—it is fundamentally eliminated.
2. Trustless by Design — Privacy Relies on Hardware, Not Integrity
TEN uses TEE to provide privacy but not to secure the ledger. This design avoids single-point trust risks and ensures users do not have to trade off chain integrity for TEE-based privacy.
3. L1 Ethereum Security — Ethereum-Grade Security and Data Availability
TEN aggregates all data and submits it to the Ethereum mainnet, using rollup architecture to reduce transaction fees and keep costs competitive with other Layer 2 solutions. Transaction finality is synchronized with Layer 1, and developers benefit from familiar Ethereum tools.
Tokenomics
$TEN has a fixed total supply of 1,000,000,000 (one billion) tokens. Its allocation is structured for sustainable growth and aims to avoid early centralization and transparency issues seen in traditional projects.
Main uses of $TEN include:
- Network governance
- Revenue sharing participation
- Payment of transaction fees and network operations
- Developer incentive programs
- Ecosystem expansion support
TEN treats its token as the network’s core resource, not as a short-term fundraising tool. Distribution is designed for gradual release, community sharing, and long-term incentives.
Token Allocation
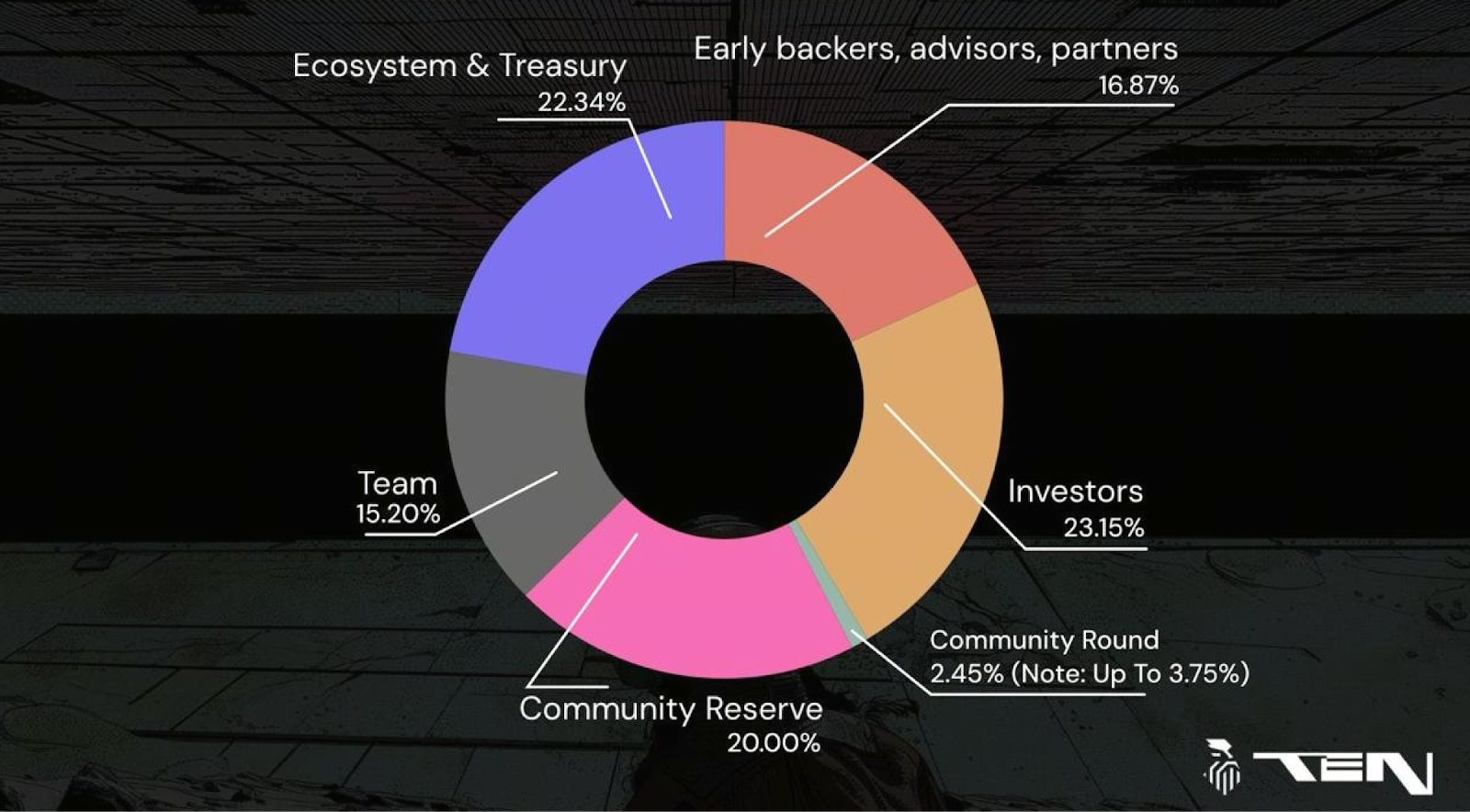
TEN’s token allocation prioritizes structure, transparency, and community engagement. The approximate breakdown is:
- 22.34% to Ecosystem & Treasury
This supports future ecosystem development, infrastructure grants, developer support, and protocol upgrades. It is TEN’s main resource pool for long-term expansion. - 16.87% to early supporters, partners, and advisors
This includes technical partners and contributors to the protocol’s early development. Distribution typically uses long-term vesting to reduce market impact. - 15.20% to the core team
Supports protocol development, engineering, and security research, with long-term vesting to align interests. - 23.15% to investors
Allocated to those who helped launch the protocol and provided resources, with a focus on long-term commitment over short-term speculation. - 2.45% to the Community Round
Up to 3.75%: Distributes TEN ownership to users to boost network participation. This is expected to serve as the main gateway for early community engagement. - 20.00% to the Community Reserve
Reserved for incentive programs, staking rewards, node participation, and project grants. This is TEN’s primary community resource pool.
(Source: tenprotocol)
TEN Future Development
TEN’s vision is not just about improving on-chain efficiency. It aims to fill a long-standing gap in Web3—the data control layer. When users can control their data, set authorization methods, and maintain unified identities across apps, the structure of on-chain economies changes. From identity and authorization to data circulation, TEN enables secure information flow and value accumulation as a core asset, instead of leaving data siloed across protocols. This marks the start of a new era for advanced Web3 applications.
To learn more about Web3, register here: https://www.gate.com/
Summary
TEN goes beyond typical Layer 2 performance. Its core value is in redefining data sovereignty. Using a unified data layer and secure authorization framework, TEN reorganizes the relationships between users, developers, and applications, giving users control over their data. This data-focused architecture provides a stronger foundation for the Web3 ecosystem, allowing future applications to grow in a more flexible and resilient environment. TEN represents not just a technical upgrade, but a significant change for the future of Web3 data.
Related Articles

What is Fartcoin? All You Need to Know About FARTCOIN

Gold Price Forecast for the Next Five Years: 2026–2030 Trend Outlook and Investment Implications, Could It Reach $6,000?

2026 Silver Price Forecast: Bull Market Continuation or High-Level Pullback? In-Depth Analysis of Silver Candlestick Chart

Crypto Future Profit Calculator: How to Calculate Your Potential Gains

Crypto Futures Calculator: Easily Estimate Your Profits & Risks


