# Web3隐私
1.6K
Qijie
From MEV Pain Points to Privacy Upgrades - TEN Protocol Reshapes Ethereum L2 Blockchain Transactions Often Subjected to MEV Attacks, Such as "Sandwich" Attacks, Resulting in Significant Losses for Users.
TEN Protocol was born out of necessity, as an Ethereum Layer 2, focusing on innovation in privacy and security.
Core Technology:
TEE-driven encryption protection TEN uses TEE (Trusted Execution Environment) hardware to encrypt transaction data, ensuring that nodes or miners cannot peek, completely thwarting MEV. Compatible with Solidity, supports smart transparency, applicable to scenarios suc
View OriginalTEN Protocol was born out of necessity, as an Ethereum Layer 2, focusing on innovation in privacy and security.
Core Technology:
TEE-driven encryption protection TEN uses TEE (Trusted Execution Environment) hardware to encrypt transaction data, ensuring that nodes or miners cannot peek, completely thwarting MEV. Compatible with Solidity, supports smart transparency, applicable to scenarios suc
- Reward
- 1
- 1
- Repost
- Share
CyberpunkDanny :
:
wait and see if ten can keep up with promises Privacy and transparency are often like fish and bear's paw, difficult to achieve both.
The public execution of smart contracts exposes data to the sunlight, with threats such as MEV attacks and front-running emerging endlessly.
By introducing TEE (Trusted Execution Environment) technology into Ethereum L2, @tenprotocol has created a "crypto black box", opening up new paths for privacy protection and verifiable computing in Web3.
In simple terms, TEN is like a secure "computational safe." Once data enters, it is processed in an encrypted environment, and the results are output to the block
View OriginalThe public execution of smart contracts exposes data to the sunlight, with threats such as MEV attacks and front-running emerging endlessly.
By introducing TEE (Trusted Execution Environment) technology into Ethereum L2, @tenprotocol has created a "crypto black box", opening up new paths for privacy protection and verifiable computing in Web3.
In simple terms, TEN is like a secure "computational safe." Once data enters, it is processed in an encrypted environment, and the results are output to the block

- Reward
- like
- Comment
- Repost
- Share
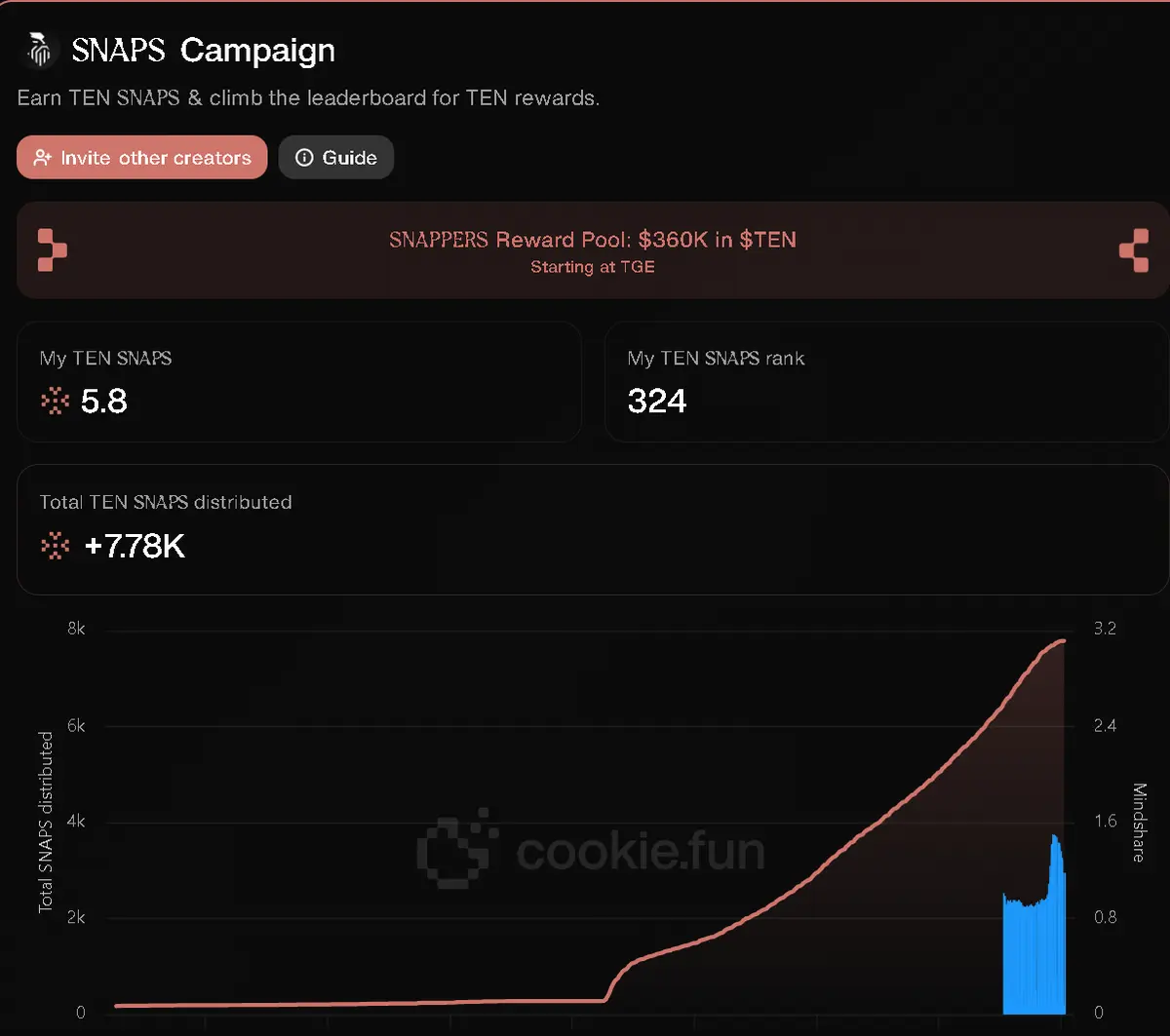
Recently, cookie rewards have been very low. Could it be that the rules have been adjusted?
@tenprotocol is expected to end on September 10th, the ranking has been stagnant, it seems it is about to wrap up!
The background of TEN is strong, developed by the original "star team" of R3 Corda. This team has a deep understanding of the pain points in blockchain and has laid a solid development path for TEN with their profound technical accumulation.
Addressing the core pain points of Web3: The transparent and traceable characteristics of blockchain provide peace of mind, but sensitive data is prone
View Original@tenprotocol is expected to end on September 10th, the ranking has been stagnant, it seems it is about to wrap up!
The background of TEN is strong, developed by the original "star team" of R3 Corda. This team has a deep understanding of the pain points in blockchain and has laid a solid development path for TEN with their profound technical accumulation.
Addressing the core pain points of Web3: The transparent and traceable characteristics of blockchain provide peace of mind, but sensitive data is prone
- Reward
- like
- Comment
- Repost
- Share
Load More
Join 40M users in our growing community
⚡️ Join 40M users in the crypto craze discussion
💬 Engage with your favorite top creators
👍 See what interests you
Trending Topics
8.92K Popularity
159.88K Popularity
30.99K Popularity
85.85K Popularity
2.61K Popularity
3.51K Popularity
2.76K Popularity
19.91K Popularity
87.22K Popularity
22.28K Popularity
211.48K Popularity
9.81K Popularity
11K Popularity
1.56K Popularity
219.09K Popularity
News
View MoreXRP (XRP Ledger) is currently trading at $1.87, with a market capitalization of approximately $113.556 billion.
5 m
The Dark Side of the Moon completes $500 million Series C funding, with IDG leading $150 million
6 m
SlowMist: Beware of browser history pollution attacks, malicious software attacks are on the rise again
14 m
SlowMist: Phishing attacks remain the primary reason for Q4 fund thefts, with 300 stolen cases recovered and $1 million USD recovered.
25 m
Family offices increase their crypto asset allocations, with volatility becoming the biggest uncertainty for 2026
27 m
Pin