MICA Daily|Forecast market bets on worsening Middle East situation, beware of weekend market volatility
2h ago
"Cryptocurrency Sell-Off" Nearing the End! JPMorgan: ETF Fund Outflows Stabilized, Worst Phase Has Passed
2h ago
Trending Topics
View More11.97K Popularity
17.28K Popularity
115 Popularity
99 Popularity
103 Popularity
Hot Gate Fun
View More- MC:$3.56KHolders:10.09%
- MC:$3.54KHolders:10.00%
- MC:$3.54KHolders:10.00%
- MC:$3.73KHolders:30.93%
- MC:$3.58KHolders:20.09%
Pin
CZ: Trust Wallet will compensate for the $7 million loss caused by the Christmas hack
The browser extension v2.68 of the Trust Wallet cryptocurrency wallet has been reported to have a security vulnerability, resulting in approximately $7 million worth of user funds being stolen. Binance founder CZ stated that Trust Wallet will fully compensate affected users for their losses and urged users of this version to take immediate measures to ensure wallet security.
Trust Wallet users encountered a carefully planned vulnerability attack on Christmas Day, ultimately losing about $7 million. Reports indicate that the attack was already being planned as early as early December. Cybersecurity firm SlowMist further stated that these malicious extensions have been exporting users’ personal information.
Trust Wallet previously posted on X that version 2.68 of the Trust Wallet browser extension was affected by a security incident, impacting desktop users. The official recommended users upgrade to version 2.69.
Related news: Trust Wallet browser extension vulnerability leads to over $6 million in user funds stolen
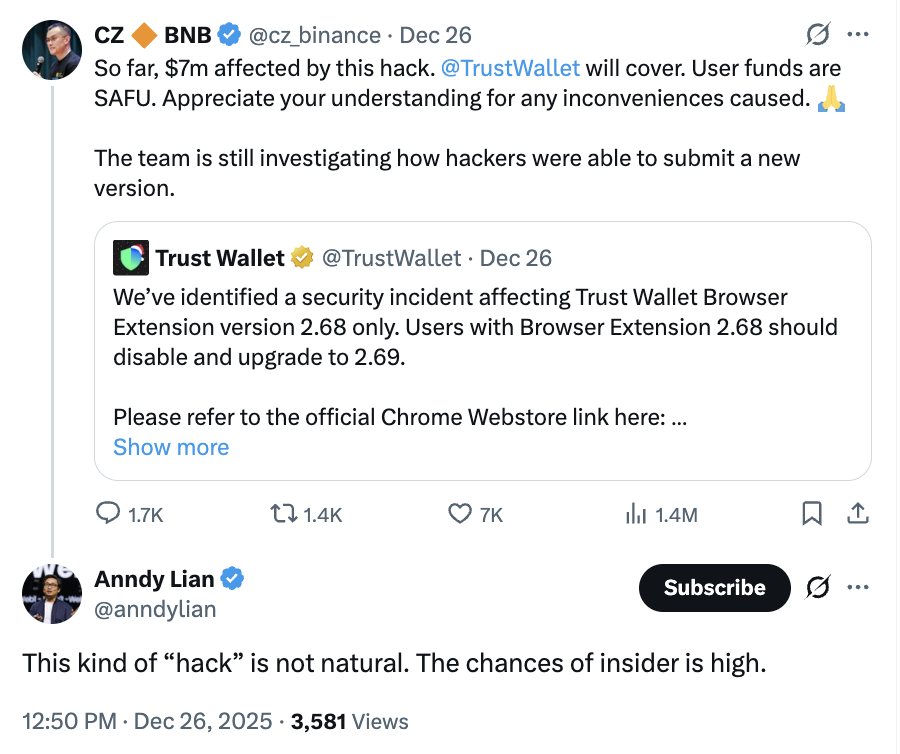
Binance co-founder CZ stated in a Friday X post that the lost funds will be compensated, “Currently, this hacker attack has caused a loss of $7 million. Compensation will be provided. User funds are SAFU.” He also mentioned that the Trust Wallet team is still investigating how the hackers managed to submit the new version.
So far, $7m affected by this hack. @TrustWallet will cover. User funds are SAFU. Appreciate your understanding for any inconveniences caused. 🙏
The team is still investigating how hackers were able to submit a new version. https://t.co/xdPGwwDU8b
— CZ 🔶 BNB (@cz_binance) December 26, 2025
Cryptocurrency wallet vulnerabilities pose an increasingly serious threat to digital asset investors. According to data from Chainalysis, the amount stolen in 2025 has exceeded $3.4 billion, with the Bybit theft in February alone resulting in an estimated loss of about $1.5 billion. In 2025, incidents of personal wallet theft surged to 158,000, affecting 80,000 different victims, but the total stolen amount ($713 million) decreased compared to 2024.
Related news: Progress in tracking the $1.4 billion stolen from Bybit: nearly 28% of the funds “cut off,” successfully frozen 3.84% of assets
Trust Wallet vulnerability raises concerns among crypto industry observers
Cos, founder of blockchain security firm SlowMist, posted that he observed the planning of the Trust Wallet attack had begun as early as December 8.
The Trust Wallet browser extension with a backdoor version is 2.68.0, and the fixed version is 2.69.0. Comparing the two, the differences between the normal code and the backdoor code are shown in the image.
The backdoor code added a PostHog to collect various privacy information of wallet users (including seed phrases) and send it to the attacker’s server api.metrics-trustwallet[.]com.
Estimated timeline: Attackers started preparations at least on 12.8… https://t.co/EpvCqRli7n pic.twitter.com/FOLjD6aPar
— Cos(Yúhéng)😶🌫️ (@evilcos) December 26, 2025
Cos pointed out that the backdoor version of the Trust Wallet browser extension is 2.68.0, and the fixed version is 2.69.0. He compared the differences between the normal and backdoor code, stating, “The backdoor code added a PostHog to collect various privacy information of wallet users (including seed phrases) and send it to the attacker’s server api.metrics-trustwallet[.]com.
Estimated timeline: The attackers started preparations at least on December 8, began implanting the backdoor on December 22, and started transferring funds on Christmas, which led to discovery.”
Some industry insiders suggest that this vulnerability exploitation may involve internal personnel activity, as the attacker was able to submit a new version of the Trust Wallet extension on the website, “This kind of ‘hacking’ is unnatural. The possibility of insider involvement is very high.”
Regarding community members’ comments: “It must be an insider (perpetrator).” CZ himself also indicated this possibility. SlowMist also pointed out that the attacker “is very familiar with the source code of Trust Wallet extensions,” which enabled the hacker to implement the backdoor code needed to collect sensitive user information.